🗼Introduction
Environment variables play a crucial role in configuring applications deployed in Kubernetes clusters. They allow developers to provide runtime configuration values to their applications without hardcoding them in the application code. Kubernetes provides ConfigMaps and Secrets as two essential resources for managing environment variables securely. In this blog, we will explore how to set environment variables in Kubernetes using ConfigMap and ensure the security of sensitive information.
🗼ConfigMap
Managing environment data directly within the pod definition files can become challenging, especially when you have a large number of pods. In such cases, utilizing ConfigMaps in Kubernetes is a recommended approach to centralize and manage configuration data efficiently. ConfigMaps allow you to store configuration information as key-value pairs separate from the pod definition files. By doing so, you decouple the configuration from the application code and gain flexibility in updating the configuration without modifying the pod definitions.
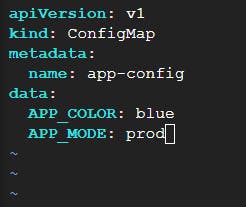
🎗️Create a ConfigMap:
Use the kubectl create configmap command to create a ConfigMap. You can provide key-value pairs either directly or by specifying a configuration file.
kubectl create configmap my-config --from-literal=KEY1=VALUE1
🎗️Reference the ConfigMap in a Pod:
Modify your pod definition file to reference the ConfigMap. You can use the env section within the container specification to define environment variables sourced from the ConfigMap.
apiVersion: v1
kind: Pod
metadata:
name: my-pod
spec:
containers:
- name: my-container
image: my-image
envFrom:
- configMapRef:
name: my-config
🎗️Apply the modified pod definition:
Apply the updated pod definition using the kubectl apply -f command.
kubectl apply -f pod.yaml
By following these steps, the ConfigMap is injected into the pod, and the key-value pairs from the ConfigMap become available as environment variables within the container running in the pod.
🗼Secrets
In Kubernetes, Secrets are used to store sensitive information such as passwords, API keys, or TLS certificates. They are similar to ConfigMaps in the sense that they provide a way to store key-value pairs, but they are specifically designed for sensitive data. The main difference between ConfigMaps and Secrets is that Secrets are encoded and stored in Base64 format and can be encrypted when stored in etcd, the Kubernetes datastore. This provides an additional layer of security for sensitive information compared to plain text ConfigMaps.
🎗️Imperative way to create secret
kubectl create secret generic <name of the secrete> --from-literal=<key>=<value>
Note: - Kubernetes Secrets are encoded using base64 to protect sensitive information from being easily readable as plain text. However, base64 encoding is not a form of encryption. It is a simple encoding scheme that transforms binary data into a readable ASCII format. It's important to note that base64 encoding is a reversible process, and the original data can be easily decoded back from the encoded form. Therefore, Secrets should not be considered secure against determined attackers or unauthorized access. Base64 encoding provides a minimal level of obfuscation but does not offer the same level of protection as encryption. To enhance the security of sensitive data stored in Secrets, additional measures should be taken.
🗼Encrypting Secret Data at Rest
To add encrypting secret data in kube-apiserver follow the steps:
Step 1: Create a secret key using the following command
head -c 32 /dev/urandom | base64
Step 2: Create a enc.yaml file in /etc/kubernetes/enc and add the following Encryption Configuration to it.
apiVersion: apiserver.config.k8s.10/V1
kind: EncryptionConfiguration
resources:
- resources:
- secrets
- configmaps
- pandas. awesome. bears. example
providers:
- aescbc:
keys:
- name: key1
secret: LVWGE2HDZBTRIrh2 GAZOuxWBkKAtOdeYPpnoYCBV.J4=
- identity: {}
Step 3: Add the following line in the manifest of kube-apiserver static pod which is located in /etc/kubernetes/manifests/kube-apiserver.yaml:
- --encryption-provider-config=/etc/kubernetes/enc/enc.yaml
Step 4:To Mount the /enc folder add the following in the volumeMount Section:
- name: enc
mountPath: /etc/kubernetes/enc
readonly: true
Step 5:Then add the following in the volume section:
- name: enc
hostPath:
path: /etc/kubernetes/enc
type: DirectoryorCreate
🗼Conclusion
Setting environment variables in Kubernetes using ConfigMaps and Secrets is an effective way to manage runtime configuration and securely handle sensitive information. ConfigMaps are ideal for non-sensitive data, while Secrets provide a secure mechanism for storing confidential information. By adhering to security best practices and using RBAC, you can ensure that your environment variables remain protected and that access to sensitive data is limited only to authorized entities.
